Summary
Assigned CVE: CVE-2020-7283 has been assigned and RedyOps Labs has been publicly acknowledged by the vendor.
Known to Neurosoft’s RedyOps Labs since: 09/03/2020
Exploit Code: https://github.com/RedyOpsResearchLabs/CVE-2020-7283-McAfee-Total-Protection-MTP-16.0.R26-EoP
An Elevation of Privilege (EoP) exists in McAfee Total Protection (MTP) < 16.0.R26 . The latest version we tested is McAfee Total Protection (MTP) 16.0.R23. The exploitation of this EoP , gives the ability to a low privileged user to create a file anywhere in the system. The file is being created with a DACL , which allows any user to edit the file. Because of this, the attacker can create a file with any chosen name.extension and edit it in order to execute the code of his choice.
If the file already exists, it will be overwritten, with an empty file.
There are many ways to abuse this issue. We chose to create a bat file in the Users Startup folder C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\backdoor.bat .
Description
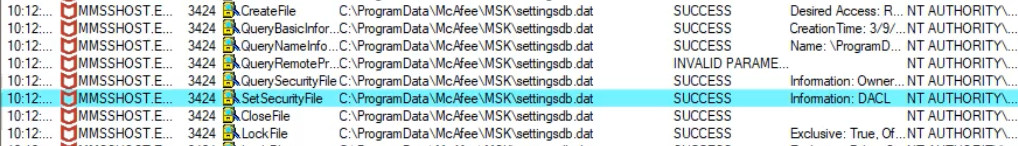
Whenever a scan is initiated, the process MMSSHOST.EXE which runs as an NT AUTHORITY\SYSTEM, and without impersonation, creates the file c:\ProgramData\McAfee\MSK\settingsdb.dat .
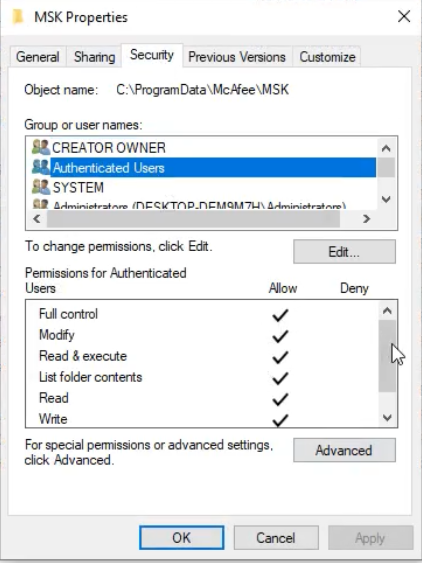
The permissions which are assigned to this file, allow to the “Authenticated Users” to have full control over the file.
When we first log into the windows system and without performing any actions, the file c:\ProgramData\McAfee\MSK\settingsdb.dat and the files MSK*.dat in the same folder, are not locked (they are not used by any program) and we have the proper permissions in order to delete them.
After we delete these files, we can make “C:\ProgramData\McAfee\MSK\settingsdb.dat”, a symlink to any chosen file.
With the symlink in place, the initiation of a scan will trigger the execution of the MMSSHOST.EXE.
At this very moment, If we initiate a scan, the MMSSHOST.EXE will try to create the file C:\ProgramData\McAfee\MSK\settingsdb.dat , it will follow the symlink and will actually create the file which is pointed by the symlink.
After that, it will set the new permissions to that file, which allows to the “Authenticated Users” to have full control over the newly created file. Most of the times, the newly created file will remain locked and we will not be able to edit it until we reboot. After the reboot, the file is unlocked and we can edit the file and add any contents we like.
Note: Although we exploited the issue by creating symlinks of the files under the path c:\ProgramData\McAfee\MSK\ , the files under the folder c:\ProgramData\McAfee\MPF\ seem to be affected as well.
Exploitation
In order to Exploit the issue, you can use our exploit from our GitHub .
In the following paragraph, a step by step explanation of the Video PoC where we use the exploit is provided.
Video PoC Step By Step
The exploit takes as an argument the file you want to create .
00:00-02:03: We present the environment. We are low privileged users and as we can see by default, the low privileged users cannot create files under the folder C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup . The folder at the moment is empty.
02:03-02:35: We run the exploit and we pass the file we want to create as argument. In this example we pass as argument the “C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\backdoor.bat”. When the exploit instructs us to scan a file, we perform the scan and the file is created.
02:35-03:23: We present the fact that attacker has full access over the file. Moreover, we add the line “notepad.exe”, which is going to execute the notepad.exe in the context of any user which perform a login into the system. This is a bat file, so you can add the code of your choice (for example a reverse shell).
3:23-end: After the exploitation, another user logs into the system. In our example the administrator. The notepad.exe is executed because of the “C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\backdoor.bat” file.
Resources
GitHub
You can find the exploit code in our GitHub at https://github.com/RedyOpsResearchLabs/SEP-14.2-Arbitrary-Write
RedyOps team
RedyOps team, uses the 0-day exploits produced by Research Labs, before vendor releases any patch. They use it in special engagements and only for specific customers.
You can find RedyOps team at https://redyops.com/
Angel
Discovered 0-days which affect marine sector, are being contacted with the Angel Team. ANGEL has been designed and developed to meet the unique and diverse requirements of the merchant marine sector. It secures the vessel’s business, IoT and crew networks by providing oversight, security threat alerting and control of the vessel’s entire network.
You can find Angel team at https://angelcyber.gr/
Illicium
Our 0-days cannot win Illicium. Today’s information technology landscape is threatened by modern adversary security attacks, including 0-day exploits, polymorphic malwares, APTs and targeted attacks. These threats cannot be identified and mitigated using classic detection and prevention technologies; they can mimic valid user activity, do not have a signature, and do not occur in patterns. In response to attackers’ evolution, defenders now have a new kind of weapon in their arsenal: Deception.
You can find Illicium team at https://deceivewithillicium.com/
Neutrify
Discovered 0-days are being contacted to the Neutrify team, in order to develop related detection rules. Neutrify is Neurosoft’s 24×7 Security Operations Center, completely dedicated to threats monitoring and attacks detection. Beyond just monitoring, Neutrify offers additional capabilities including advanced forensic analysis and malware reverse engineering to analyze incidents.
You can find Neutrify team at https://neurosoft.gr/contact/
